🌟How internet connects the world?
Earlier I used to think that internet connections are above the cloud with satellite but it's not true, in fact internet connections are under the ocean by undersea cables. These cables connect every network in the world
This is how undersea cable connection looks like.

🌟What is client and server?
There are hundreds of millions of computers on the Net, but they all don't have same operations. Some of them are like electronic filing cabinets that simply store information and pass it on when requested. These machines are called servers. Machines that hold ordinary documents are called file servers; ones those hold people's mail details and are called mail servers; and the ones that hold Web pages are known as Web servers. There are tens of millions of servers on the Internet.
A computer that gets information from a server is called a client. When your computer connects with the Internet and with mail server at your ISP (Internet Service Provider) so you can read your messages, in this case your computer is the client and the ISP computer is the server. There are far more clients on the Internet than servers—billions of them, if you count smartphones as well !

🌟How communication happens between computers:
Guided way
Unguided way
Connection of network by physical entity eg: optical cables, coaxial cables etc.
Connection of network by wireless entity eg: Bluetooth, wifi, 3g, 5g etc.
🌟Types of Computer Networks
A computer network is a group of computers linked together that allows them to communicate with each other and share resources, data, and applications. Networks can vary in size and complexity, and they can be categorized into four main types:✍
Local Area Networks (LANs)
Personal Area Networks (PANs)
Metropolitan Area Networks (MANs)
Wide Area Networks (WANs).
🌟OSI Model

Application layer
Application layer is implemented in software
From the application layer data is send to presentation layer.
Presentation layer
The presentation layer converts the data(image, videos) into machine representable binary format Extended binary coded decimal interchange code translation
Before that it encodes, encryption provides abstraction, as compressed SSL protocol is used here.
Then data is send from presentation layer to session layer.
Session layer
It helps in setting up and managing connections and it enables the sending and receiving of data followed by the termination of connective data
Authentication and authorization.
Transport layer
Data transformed from session to transport layer
It is responsible for the transport of data eg: UDP & TCP
It has segments, port number, sequence number, flow control and error control
It adds some checksum to every data to check whether it has completed transferred successfully
TCP -> Connection oriented transmission ( eg: email)
UDP -> Connectionless oriented transmission and its is faster ( eg: video call)
Network layer
Then data is transferred to network layer
This is transmitted if the received data segment from one computer to another that is located in different location
Logical addressing (IP addressing) & Load balance
It assigns IP address to sender and receiver to all the layer
Data link layer
It allows to communicate directly to host and computers
Physical addressing(MAC) is done in data link layer
It's a 12 digit alpha numeric value
Adds mac address in frame and pushes to layers
Physical layer
- It contains hardware like cables.etc
🌟Protocols
Network protocols are a set of rules outlining how connected devices communicate across a network to exchange information easily and safely.
Example
HTTP -> (Hyper Text Transfer Protocol)
DHCP -> (Dynamic Host Control Protocol)
FTP -> (File Transfer Protocol)
SMTP -> (Simple Mail Transfer Protocol)
POP3 -> (Post Office Protocol)
IMAP -> (Internet Message Access Protocol)
SSH -> (Secure Shell)
VNC -> (Virtual Network Computing)
Data are called by different names at different layers:
Transport layer -> Segments
Network layer -> Packets
Data link layer -> Frames
🌟STATUS CODE
Every request has a status code which is used to know the status about that request,
1 x x -> Information
2 x x -> Success
3 x x -> Redirecting
4 x x -> Client error
5 x x -> Server error
🌟Network Security
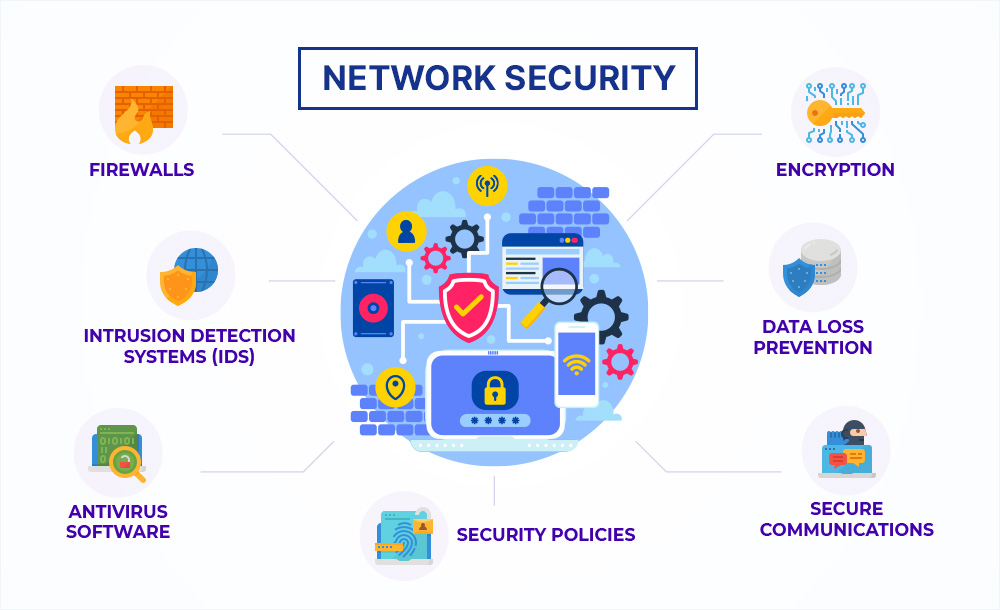
Threats and Vulnerabilities:
Hackers, malware, and viruses constantly seek to exploit weaknesses in the network.
Data breaches: Sensitive information can be stolen through unauthorized access.
Denial-of-service (DoS) attacks: Flooding your network with traffic can render it unusable for legitimate users.
Network Security Devices:
Firewalls: Controls incoming and outgoing of network traffic.
Intrusion Detection Systems (IDS): Monitor network activity for suspicious behavior and potential attacks.
Intrusion Prevention Systems (IPS): Actively block malicious traffic identified by an IDS.
Network Security Practices:
Encryption: Secure sensitive data both in transit and at rest.
Strong passwords
Software updates
User access control
Virtual Private Network (VPN):
Creates a secure tunnel for encrypted communication over a public network.
Protects data confidentiality and privacy, especially on unsecured Wi-Fi.
🌟Network Management

Network Monitoring
Constantly checks network health, identifying performance issues and potential bottlenecks.
Tools track metrics like bandwidth usage, latency, and packet loss.
Proactive monitoring helps prevent outages and ensures optimal network performance.
Network Troubleshooting:
The art of diagnosing and resolving network problems when things go wrong.
Involves analyzing logs, testing connectivity, and identifying root causes of issues.
Effective troubleshooting skills are crucial for maintaining network uptime.
Configuration Management:
Automates the process of configuring network devices like routers and switches.
Ensures consistent configurations across all devices, minimizing errors.
Tools can automate repetitive tasks, saving time and resources.
🌟Conclusion
Computer networks are essential in today's world, enabling people and devices to communicate and share information across different locations. We discussed the different types of computer networks including LAN, WAN.etc and the protocols used in each network.
Overall, computer networks play a critical role in our daily lives and it is essential to stay up-to-date with the latest technologies and security practices to maintain their reliability and security.
