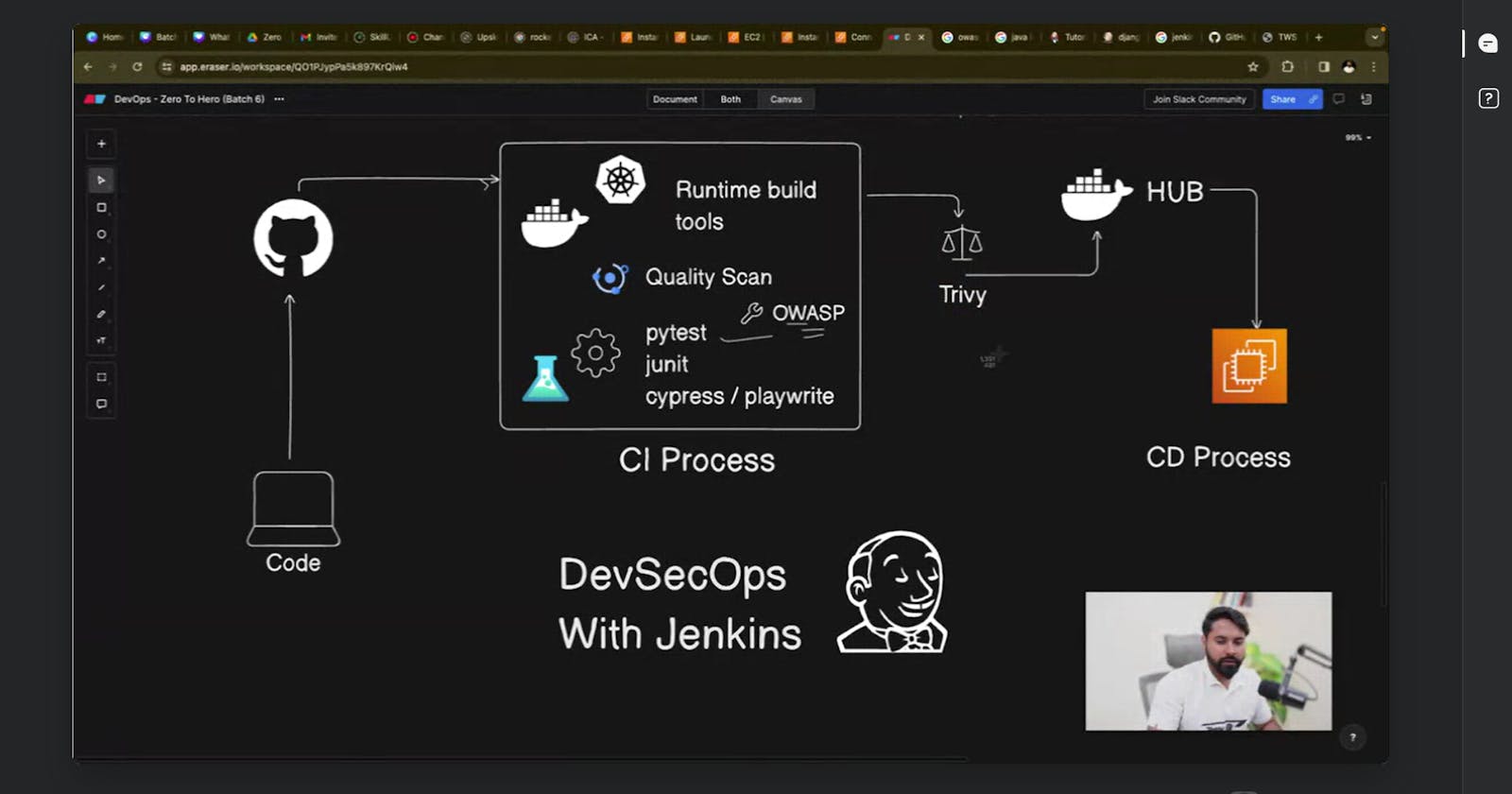
✨Building a Secure CI/CD Pipeline with DevSecOps in Jenkins.
In today's fast-paced development environment, security is paramount. DevSecOps practices integrate security considerations throughout the software development lifecycle (SDLC). This blog post dives into how to leverage Jenkins, a popular open-source automation server, to create a secure CI/CD pipeline using a declarative pipeline approach. We'll be incorporating industry-standard tools like Docker, SonarQube, a testing framework, OWASP dependency checker, Trivy, Docker Compose, and AWS Cloud for a robust and secure development process.
Why DevSecOps with Jenkins?
Shift Left Security: By integrating security checks into the pipeline, vulnerabilities are identified and addressed earlier, saving time and resources.
Automation: Automating security testing ensures consistency and reduces human error.
Improved Collaboration: DevSecOps fosters better communication between developers, security teams, and operations personnel.
Building the Pipeline:
Declarative Pipeline Setup: Configure your Jenkins pipeline using a Jenkinsfile. This code defines the pipeline stages, including building, testing, security scanning, and deployment.
Docker Integration: Leverage Docker containers to ensure consistent build environments across development, testing, and deployment stages.
SonarQube for Code Quality: Integrate SonarQube to analyze code for potential security vulnerabilities, code smells, and bugs.
Test Framework Integration: Select a suitable testing framework (e.g., JUnit, PHPUnit) to automate unit and integration tests.
OWASP Dependency Check: Utilize the OWASP Dependency Check plugin to scan dependencies for known vulnerabilities.
Trivy for Container Security: Integrate Trivy to scan Docker images for vulnerabilities in container base layers and application dependencies.
Docker Compose Integration: Utilize Docker Compose to manage multi-container applications and simplify deployment to AWS Cloud.
AWS Cloud Deployment: Configure Jenkins to deploy your application to AWS services like Amazon Elastic Container Service (ECS) or Elastic Beanstalk.
Benefits of this Approach:
Early Vulnerability Detection: Security scans throughout the pipeline identify and address vulnerabilities early.
Improved Code Quality: SonarQube helps maintain clean and maintainable code.
Automated Testing: Ensures code functionality and reduces the risk of regressions.
Secure Deployment: Trivy scans guarantee secure container deployments.
Scalable Infrastructure: Docker Compose simplifies deployments to cloud environments like AWS.
By implementing this DevSecOps approach with Jenkins, you can significantly enhance the security and quality of your software development process, fostering a culture of collaboration and continuous improvement.
Happy learning !!